In an increasingly interconnected world, securing industrial control systems (ICS) has become a critical concern for manufacturing companies. One widely recognized approach to ICS security is the Purdue Model, also known as the Purdue Enterprise Reference Architecture. Developed by the Purdue University’s Center for Education and Research in Information Assurance and Security (CERIAS), this model provides a framework for organizing and securing control systems in manufacturing environments.
Understanding the Purdue Model
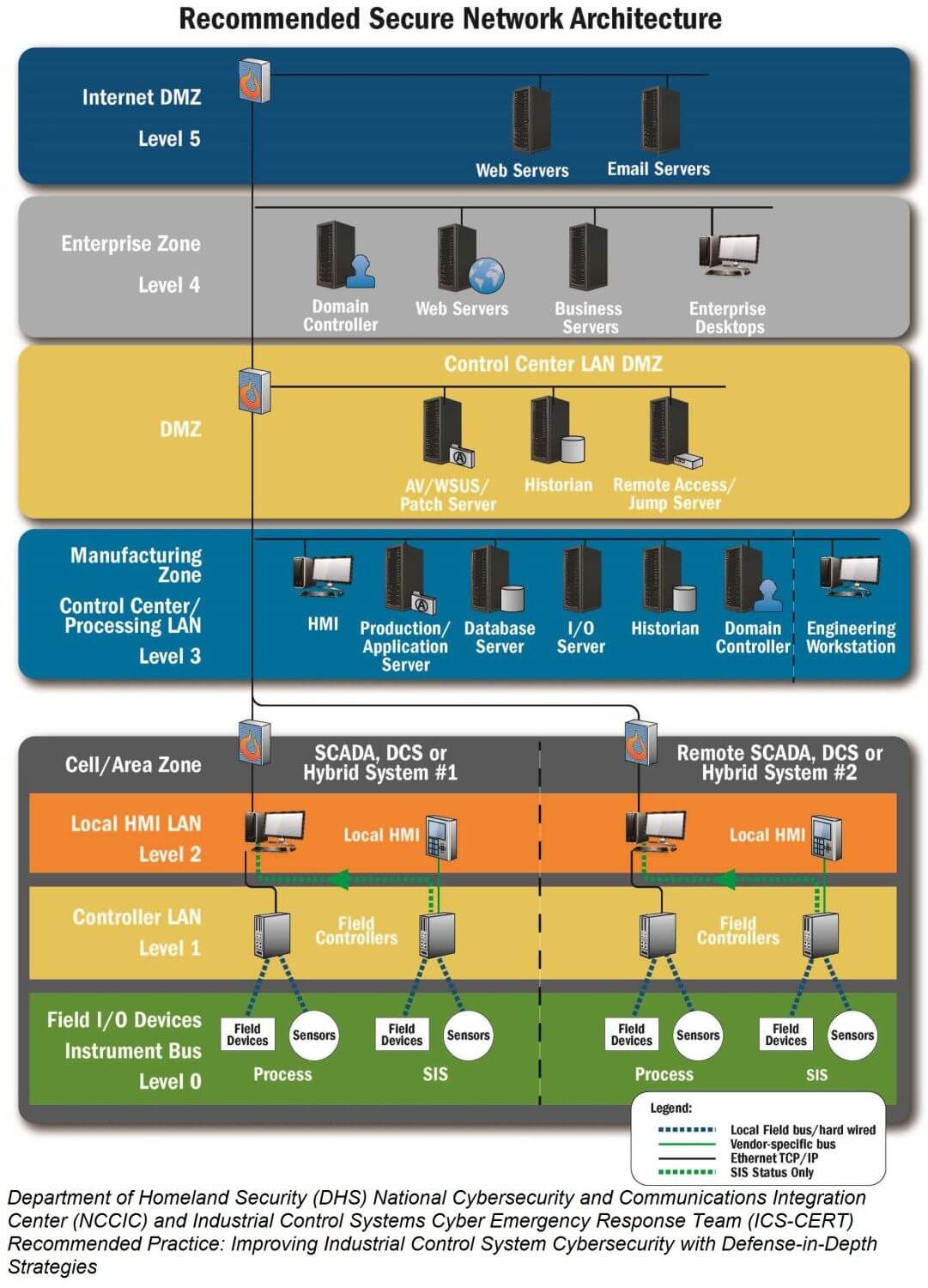
The Purdue Model is based on the concept of hierarchical levels, each responsible for specific functions and security controls within a manufacturing system. These levels, also known as zones, provide a structured approach to secure ICS components and ensure the integrity, availability, and confidentiality of critical operations.
Level 0: Physical Processes
At the bottom of the hierarchy lies Level 0, representing the physical processes in a manufacturing environment. This includes sensors, actuators, motors, and other devices directly involved in the production process. As these devices interact with the physical world, they typically don’t have built-in security mechanisms.
Level 1: Basic Control
Level 1 comprises basic control functions such as distributed control systems (DCS) and programmable logic controllers (PLC). These devices handle discrete and analog control of the physical processes found at Level 0. Security measures at this level focus on access controls and protecting against unauthorized modifications.
Level 2: Supervisory Control
Level 2 encompasses the supervisory control layer, responsible for monitoring and managing Level 1 devices. It consists mainly of supervisory control and data acquisition (SCADA) systems, which collect, process, and visualize data from Level 1 controllers. Security measures at this level include intrusion detection systems, data authentication, and secure communication protocols.
Level 3: Manufacturing Operations
Level 3 represents the manufacturing operations layer, which is responsible for managing production schedules, quality control, and resource allocation. This layer typically includes manufacturing execution systems (MES) and enterprise resource planning (ERP) systems. Security measures focus on protecting sensitive data, ensuring data integrity, and preventing unauthorized access.
Level 4: Business Planning
At the top of the hierarchy is Level 4, covering the business planning layer. This includes enterprise-level systems such as customer relationship management (CRM) and financial management software. Security efforts concentrate on safeguarding critical business information, preventing data breaches, and defending against cyber threats.
Key Security Challenges and Measures
Implementing the Purdue Model of Security for Manufacturing comes with its own set of challenges. One prominent challenge is the need to balance security measures with the continuous operation of critical processes. Moreover, manufacturers must contend with the ever-evolving threat landscape.
To address these challenges, several security measures can be implemented:
- Segmentation and isolation: Each level should be isolated and protected through proper network segmentation, access controls, and firewalls to limit the potential impact of an attack.
- Strong authentication and authorization: Applying robust authentication mechanisms, such as two-factor authentication, can prevent unauthorized access to critical control systems.
- Continuous monitoring: Regular monitoring of network traffic, system logs, and anomaly detection systems enables the timely identification of security incidents and potential threats.
- Security patches and updates: A proactive approach to regularly applying security patches and updates can help mitigate vulnerabilities in the system.
- Employee training and awareness: Manufacturing personnel should receive training to recognize and respond to potential security threats, including social engineering attacks and phishing attempts.
- Backup and disaster recovery: Regular data backups and robust disaster recovery plans help minimize the impact of a security incident and ensure business continuity.
Embracing a Secure Future
The Purdue Model of Security for Manufacturing offers a systematic approach to protect industrial control systems from cyber threats. By adopting this model and implementing comprehensive security measures, manufacturing companies can safeguard their critical processes, maintain productivity, and ensure the safety of their employees and customers. With the increasing prominence of smart factories and the Industrial Internet of Things (IIoT), it is more important than ever to prioritize the security of our industrial infrastructures.